授權(quán)最佳實(shí)踐
容器計(jì)算服務(wù) ACS(Container Compute Service)的授權(quán)體系包含對(duì)基礎(chǔ)計(jì)算資源的RAM授權(quán)和對(duì)ACS類型ACK集群側(cè)RBAC授權(quán),不同用戶角色在這兩個(gè)層面都具有不同的權(quán)限要求。本文介紹針對(duì)企業(yè)資源管理人員,Kubernetes集群管理人員,以及集群與應(yīng)用運(yùn)維人員、應(yīng)用開發(fā)人員、權(quán)限管理人員五類對(duì)象的授權(quán)最佳實(shí)踐。
ACS授權(quán)體系
ACS的授權(quán)體系包含對(duì)基礎(chǔ)資源層的RAM授權(quán)以及對(duì)ACS集群層的RBAC授權(quán)。ACS授權(quán)體系如下圖所示。

RAM授權(quán)包括對(duì)集群的運(yùn)維操作,因?yàn)锳CS集群是 ACK 的一種 Serverless K8s 集群類型,對(duì)ACS集群的運(yùn)維操作需要通過ACK OpenAPI執(zhí)行,所以需要獲取ACK產(chǎn)品及其所依賴的阿里云產(chǎn)品的OpenAPI操作權(quán)限,主要包括以下操作:
集群:創(chuàng)建、查看、刪除。
集群RBAC授權(quán)管理。
集群監(jiān)控、日志、事件。
RBAC授權(quán)對(duì)應(yīng)的是運(yùn)行于ACS集群中Kubernetes應(yīng)用的運(yùn)維操作,需要獲取ACS集群及其命名空間的操作權(quán)限,主要包括對(duì)以下Kubernetes對(duì)象的增刪改查操作:
工作負(fù)載:Deployment、StatefulSet、Job、CronJob、Pod、ReplicaSet、HPA等。
網(wǎng)絡(luò):Service、Ingress、NetworkPolicy等。
存儲(chǔ):PV、PVC、StorageClass等。
Namespace、ConfigMap、Secrets等。
系統(tǒng)默認(rèn)授權(quán)策略
容器計(jì)算服務(wù)ACS預(yù)置以下系統(tǒng)授權(quán)策略,您可以通過給RAM用戶或RAM角色授權(quán)系統(tǒng)默認(rèn)授權(quán)策略,完成快速授權(quán)。
系統(tǒng)默認(rèn)授權(quán)策略授權(quán)范圍較大,可具有ACK、ACS所有OpenAPI的讀或?qū)憴?quán)限,請(qǐng)謹(jǐn)慎授權(quán)。
系統(tǒng)默認(rèn)授權(quán)策略 | 授權(quán)策略描述 |
AliyunAccFullAccess | 管理容器計(jì)算服務(wù)ACS的權(quán)限。 |
AliyunAccReadOnlyAccess | 只讀訪問容器計(jì)算服務(wù)ACS的權(quán)限。 |
AliyunCSFullAccess | 管理容器服務(wù)ACK的權(quán)限。 重要 可讀寫操作包括ACS類型在內(nèi)所有ACK集群的,請(qǐng)謹(jǐn)慎授權(quán)。 |
AliyunCSReadOnlyAccess | 只讀訪問容器服務(wù)ACK的權(quán)限。 重要 可讀操作包括ACS類型在內(nèi)所有ACK集群的,請(qǐng)謹(jǐn)慎授權(quán)。 |
AliyunAccFullAccess授權(quán)策略
{
"Statement": [
{
"Effect": "Allow",
"Action": "acc:*",
"Resource": "*"
}
],
"Version": "1"
}AliyunAccReadOnlyAccess授權(quán)策略
{
"Version": "1",
"Statement": [
{
"Action": [
"acc:Describe*",
"acc:CheckServiceRole"
],
"Resource": "*",
"Effect": "Allow"
}
]
}AliyunCSFullAccess授權(quán)策略
{
"Version": "1",
"Statement": [
{
"Action": "cs:*",
"Resource": "*",
"Effect": "Allow"
},
{
"Action": "ram:PassRole",
"Resource": "*",
"Effect": "Allow",
"Condition": {
"StringEquals": {
"acs:Service": "cs.aliyuncs.com"
}
}
}
]
}AliyunCSReadOnlyAccess授權(quán)策略
{
"Version": "1",
"Statement": [
{
"Action": [
"cs:CheckServiceRole",
"cs:Get*",
"cs:List*",
"cs:Describe*"
],
"Resource": "*",
"Effect": "Allow"
}
]
}授權(quán)最佳實(shí)踐
當(dāng)RAM用戶或RAM角色需要進(jìn)行集群運(yùn)維和應(yīng)用運(yùn)維時(shí),您需要依次對(duì)其進(jìn)行RAM授權(quán)和RBAC授權(quán)。在進(jìn)行RBAC授權(quán)之前,您需要先進(jìn)行RAM授權(quán)。三種典型場(chǎng)景的授權(quán)操作如下:
如果授權(quán)對(duì)象為集群與集群內(nèi)應(yīng)用的運(yùn)維人員,請(qǐng)參見場(chǎng)景一:授權(quán)對(duì)象為集群與集群內(nèi)應(yīng)用的運(yùn)維人員。
如果授權(quán)對(duì)象為集群內(nèi)應(yīng)用的開發(fā)人員,請(qǐng)參見場(chǎng)景二:授權(quán)對(duì)象為集群內(nèi)應(yīng)用的開發(fā)人員。
如果授權(quán)對(duì)象為集群內(nèi)應(yīng)用的權(quán)限管理員,請(qǐng)參見場(chǎng)景三:授權(quán)對(duì)象為集群內(nèi)應(yīng)用的權(quán)限管理員。
場(chǎng)景一:授權(quán)對(duì)象為集群與集群內(nèi)應(yīng)用的運(yùn)維人員
授權(quán)對(duì)象需要管理和運(yùn)維ACS集群所需的必要權(quán)限,同時(shí)有ACS集群內(nèi)應(yīng)用資源對(duì)象的運(yùn)維需求。因此授權(quán)流程包含RAM授權(quán)和RBAC授權(quán)。
RAM授權(quán)
容器服務(wù)ACK在RAM側(cè)提供了AliyunCSFullAccess和AliyunCSReadOnlyAccess兩個(gè)系統(tǒng)策略。
AliyunCSFullAccess包含了容器服務(wù)ACK全部OpenAPI的讀寫訪問權(quán)限。
AliyunCSReadOnlyAccess包含了容器服務(wù)ACK全部OpenAPI的只讀訪問權(quán)限。
重要以上兩個(gè)系統(tǒng)策略授權(quán)操作包括ACS類型在內(nèi)所有ACK集群的,請(qǐng)謹(jǐn)慎授權(quán)。
您需要登錄RAM管理控制臺(tái),根據(jù)需要選擇綁定其中一個(gè)系統(tǒng)策略。具體操作,請(qǐng)參見為RAM用戶授權(quán)和為RAM角色授權(quán)。
如果您有細(xì)粒度權(quán)限控制的需求,可以自定義授權(quán)策略。具體操作,請(qǐng)參見為RAM用戶或RAM角色授予RAM權(quán)限。
此場(chǎng)景下,RAM授權(quán)策略示例如下所示。
{ "Statement": [ { "Effect": "Allow", "Action": [ "acc:DescribeCommodityStatus", "acc:CheckServiceRole", "acc:DescribeCloudProducts", "acc:DescribeRegions", "acc:DescribeZones", "acc:GetInstancePrice" ], "Resource": "*" }, { "Effect": "Allow", "Action": "bssapi:GetPayAsYouGoPrice", "Resource": "*" }, { "Action": "ecs:DescribePrice", "Effect": "Allow", "Resource": "*" }, { "Action": "ram:GetRole", "Effect": "Allow", "Resource": "*" }, { "Action": [ "cs:CreateCluster", "cs:DescribeAddons" ], "Effect": "Allow", "Resource": "*" }, { "Action": [ "cs:GetClusters", "cs:DescribeClustersV1", "cs:DescribeClusterUserKubeconfig", "cs:DescribeClusterResources", "cs:DescribeUserQuota", "cs:DescribeClusterLogs", "cs:ModifyCluster", "cs:UpgradeCluster", "cs:GetUpgradeStatus", "cs:ResumeUpgradeCluster", "cs:PauseClusterUpgrade", "cs:CancelClusterUpgrade", "cs:InstallClusterAddons", "cs:UpgradeClusterAddons", "cs:DescribeClusterAddonsUpgradeStatus", "cs:UnInstallClusterAddons", "cs:DeleteCluster", "cs:DescribeClusterDetail", "cs:GetClusterAuditProject", "cs:DescribeClusterAddonsVersion", "cs:DescribeClusterTasks", "cs:DescribeClusterEvents", "cs:DescribeEvents", "cs:ListClusterReportSummary", "cs:GetClusterBasicInfo", "cs:ListReportTaskRule", "cs:CreateReportTaskRule", "cs:CreateClusterCheck" ], "Effect": "Allow", "Resource": "acs:cs:*:*:cluster/<yourclusterID>" }, { "Action": [ "cs:CheckServiceRole", "cs:DescribeKubernetesVersionMetadata" ], "Effect": "Allow", "Resource": "acs:cs:*:*:cluster/*" }, { "Action": [ "log:ListProject" ], "Effect": "Allow", "Resource": "*" }, { "Action": [ "vpc:ListEnhanhcedNatGatewayAvailableZones", "vpc:DescribeEipAddresses" ], "Effect": "Allow", "Resource": "*" } ], "Version": "1" }上面示例中
<yourclusterID>需要替換成實(shí)際ACS集群ID。關(guān)于容器服務(wù)ACK OpenAPI的更多說明,請(qǐng)參見【產(chǎn)品變更】容器服務(wù)OpenAPI鑒權(quán)優(yōu)化公告和API概覽。
RBAC授權(quán)
完成RAM授權(quán)后,您還需要為RAM用戶或RAM角色授予對(duì)應(yīng)集群的RBAC權(quán)限。容器服務(wù)ACK在集群層面提供了四種預(yù)置角色。
角色
集群內(nèi)RBAC權(quán)限
管理員
對(duì)所有命名空間下所有資源有讀寫權(quán)限。
運(yùn)維人員
對(duì)所有命名空間下控制臺(tái)可見Kubernetes資源有讀寫權(quán)限,對(duì)集群節(jié)點(diǎn)、存儲(chǔ)卷、命名空間、配額有只讀權(quán)限。
開發(fā)人員
對(duì)所有命名空間或所選命名空間下控制臺(tái)可見Kubernetes資源有讀寫權(quán)限。
受限用戶
對(duì)所有命名空間或所選命名空間下控制臺(tái)可見Kubernetes資源有只讀權(quán)限。
此場(chǎng)景下,您可以容器計(jì)算服務(wù)控制臺(tái)授權(quán)管理頁面,為授權(quán)對(duì)象配置目標(biāo)集群和對(duì)應(yīng)命名空間的訪問權(quán)限為運(yùn)維人員。
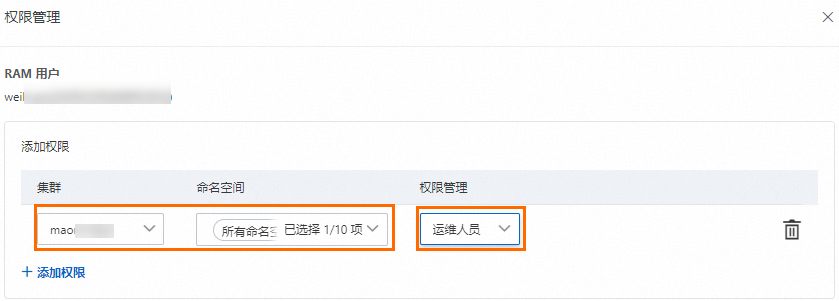
綁定預(yù)置角色后,ACS會(huì)自動(dòng)在集群中創(chuàng)建與被授權(quán)對(duì)象身份對(duì)應(yīng)的ClusterRoleBinding實(shí)例。預(yù)置運(yùn)維人員角色的RBAC權(quán)限如下所示。
apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: cs:ops rules: - apiGroups: [""] resources: ["pods", "pods/attach", "pods/exec", "pods/portforward", "pods/proxy"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: [""] resources: ["configmaps", "endpoints", "persistentvolumeclaims", "replicationcontrollers", "replicationcontrollers/scale", "secrets", "serviceaccounts", "services", "services/proxy"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: [""] resources: ["bindings", "events", "limitranges", "namespaces/status", "replicationcontrollers/status", "pods/log", "pods/status", "resourcequotas", "resourcequotas/status", "componentstatuses"] verbs: ["get", "list", "watch"] - apiGroups: [""] resources: ["namespaces", "nodes", "persistentvolumes"] verbs: ["get", "list", "watch", "patch"] - apiGroups: ["coordination.k8s.io"] resources: ["leases"] verbs: ["get"] - apiGroups: ["apps"] resources: ["daemonsets", "deployments", "deployments/rollback", "deployments/scale", "replicasets", "replicasets/scale", "statefulsets"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: ["autoscaling"] resources: ["horizontalpodautoscalers"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: ["batch"] resources: ["cronjobs", "jobs"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: ["extensions"] resources: ["daemonsets", "deployments", "deployments/rollback", "deployments/scale","ingresses","replicasets", "replicasets/scale", "replicationcontrollers/scale"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: ["networking.k8s.io"] resources: ["*"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: ["servicecatalog.k8s.io"] resources: ["clusterserviceclasses", "clusterserviceplans", "clusterservicebrokers", "serviceinstances", "servicebindings"] verbs: ["create", "delete", "get", "list", "patch", "update", "watch"] - apiGroups: ["servicecatalog.k8s.io"] resources: ["clusterservicebrokers/status", "clusterserviceclasses/status", "clusterserviceplans/status", "serviceinstances/status", "serviceinstances/reference", "servicebindings/status",] verbs: ["update"] - apiGroups: ["storage.k8s.io"] resources: ["storageclasses"] verbs: ["get", "list", "watch"] - apiGroups: ["alicloud.com"] resources: ["*"] verbs: ["create", "delete", "get", "list", "patch", "update", "watch"] - apiGroups: ["policy"] resources: ["poddisruptionbudgets"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: ["metrics.k8s.io"] resources: ["pods"] verbs: ["get", "watch", "list"] - apiGroups: ["networking.istio.io"] resources: ["*"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: ["config.istio.io"] resources: ["*"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: ["rbac.istio.io"] resources: ["*"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: ["istio.alibabacloud.com"] resources: ["*"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: ["authentication.istio.io"] resources: ["*"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: ["log.alibabacloud.com"] resources: ["*"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: ["monitoring.kiali.io"] resources: ["*"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: ["kiali.io"] resources: ["*"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: ["apiextensions.k8s.io"] resources: ["customresourcedefinitions"] verbs: ["get", "list", "create", "watch", "patch", "update", "delete", "deletecollection"] - apiGroups: ["serving.knative.dev"] resources: ["*"] verbs: ["get", "list", "create", "watch", "patch", "update", "delete", "deletecollection"] - apiGroups: ["eventing.knative.dev"] resources: ["*"] verbs: ["get", "list", "create", "watch", "patch", "update", "delete", "deletecollection"] - apiGroups: ["messaging.knative.dev"] resources: ["*"] verbs: ["get", "list", "create", "watch", "patch", "update", "delete", "deletecollection"] - apiGroups: ["sources.eventing.knative.dev"] resources: ["*"] verbs: ["get", "list", "create", "watch", "patch", "update", "delete", "deletecollection"] - apiGroups: ["tekton.dev"] resources: ["*"] verbs: ["get", "list", "create", "watch", "patch", "update", "delete", "deletecollection"] - apiGroups: ["alert.alibabacloud.com"] resources: ["*"] verbs: ["get", "list", "create", "watch", "patch", "update", "delete", "deletecollection"]如果您有細(xì)粒度的RBAC權(quán)限控制需求,可以參考RBAC創(chuàng)建自定義ClusterRole實(shí)例,然后在容器計(jì)算服務(wù)控制臺(tái)授權(quán)管理頁面選擇自定義角色,再從下拉列表中選擇自定義的ClusterRole名稱。具體操作,請(qǐng)參見自定義RBAC授權(quán)策略。
場(chǎng)景二:授權(quán)對(duì)象為集群內(nèi)應(yīng)用的開發(fā)人員
授權(quán)對(duì)象只需要擁有ACS類型ACK集群內(nèi)Kubernetes資源對(duì)象的操作權(quán)限(即RBAC授權(quán)),無需云上資源的訪問權(quán)限。
在進(jìn)行RBAC授權(quán)之前,授權(quán)對(duì)象需要至少具有目標(biāo)集群的容器服務(wù)只讀權(quán)限(即RAM授權(quán))。授權(quán)Action及Resource “*” 代表授予RAM用戶或RAM角色包括ACS類型集群在內(nèi)所有ACK集群的授權(quán)Action操作,所以請(qǐng)盡量不要將Resource置為“*”,除非您充分了解授權(quán)范圍及影響,有目的性地進(jìn)行全部授權(quán)。
RAM授權(quán)
您需要在RAM管理控制臺(tái),新增自定義策略,并將該策略授權(quán)給目標(biāo)RAM用戶或RAM角色。具體操作,請(qǐng)參見為RAM用戶或RAM角色授予RAM權(quán)限。自定義策略內(nèi)容如下所示:
{ "Statement": [ { "Effect": "Allow", "Action": [ "acc:DescribeCommodityStatus", "acc:CheckServiceRole", "acc:DescribeCloudProducts", "acc:DescribeRegions", "acc:DescribeZones", "acc:GetInstancePrice" ], "Resource": "*" }, { "Effect": "Allow", "Action": "bssapi:GetPayAsYouGoPrice", "Resource": "*" }, { "Action": [ "cs:Get*", "cs:List*", "cs:Check*", "cs:Describe*" ], "Effect": "Allow", "Resource": [ "acs:cs:*:*:cluster/<yourclusterID>"。 ] }, { "Action": [ "vpc:ListEnhanhcedNatGatewayAvailableZones", "vpc:DescribeEipAddresses" ], "Effect": "Allow", "Resource": "*" } ], "Version": "1" }上面示例中
<yourclusterID>需要替換成實(shí)際ACS集群ID。說明如果您只需要為授權(quán)對(duì)象添加ACS類型ACK集群的只讀權(quán)限,請(qǐng)務(wù)必通過該示例指定ACS類型ACK集群ARN,不可以為其添加容器服務(wù)ACK提供的RAM系統(tǒng)策略
AliyunCSReadOnlyAccess,否則將會(huì)為授權(quán)對(duì)象添加除ACS類型以外所有ACK集群的只讀權(quán)限。RBAC授權(quán)
您需要在容器計(jì)算服務(wù)控制臺(tái)授權(quán)管理頁面,為授權(quán)對(duì)象(RAM用戶或RAM角色)配置目標(biāo)集群和對(duì)應(yīng)命名空間的訪問權(quán)限為開發(fā)人員。
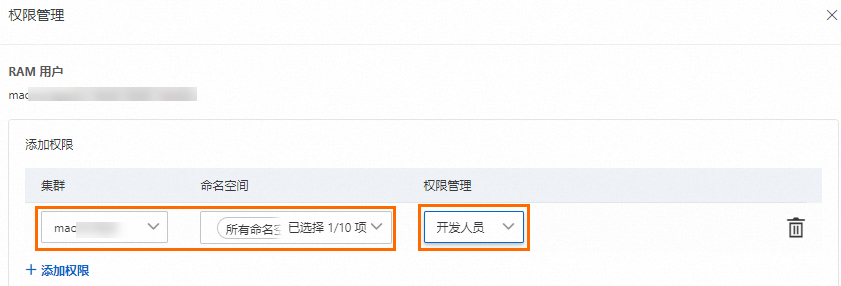
綁定預(yù)置角色后,ACS會(huì)自動(dòng)在集群中創(chuàng)建與被授權(quán)對(duì)象身份對(duì)應(yīng)的ClusterRoleBinding實(shí)例。預(yù)置開發(fā)人員角色的RBAC權(quán)限如下所示。
apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: cs:ns:dev rules: - apiGroups: [""] resources: ["pods", "pods/attach", "pods/exec", "pods/portforward", "pods/proxy"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: [""] resources: ["configmaps", "endpoints", "persistentvolumeclaims", "replicationcontrollers", "replicationcontrollers/scale", "secrets", "serviceaccounts", "services", "services/proxy"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: [""] resources: ["events", "replicationcontrollers/status", "pods/log", "pods/status"] verbs: ["get", "list", "watch"] - apiGroups: ["apps"] resources: ["daemonsets", "deployments", "deployments/rollback", "deployments/scale", "replicasets", "replicasets/scale", "statefulsets"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: ["autoscaling"] resources: ["horizontalpodautoscalers"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: ["batch"] resources: ["cronjobs", "jobs"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: ["extensions"] resources: ["daemonsets", "deployments", "deployments/rollback", "deployments/scale","ingresses","replicasets", "replicasets/scale", "replicationcontrollers/scale"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: ["networking.k8s.io"] resources: ["*"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: ["servicecatalog.k8s.io"] resources: ["clusterserviceclasses", "clusterserviceplans", "clusterservicebrokers", "serviceinstances", "servicebindings"] verbs: ["create", "delete", "get", "list", "patch", "update", "watch"] - apiGroups: ["servicecatalog.k8s.io"] resources: ["clusterservicebrokers/status", "clusterserviceclasses/status", "clusterserviceplans/status", "serviceinstances/status", "serviceinstances/reference", "servicebindings/status",] verbs: ["update"] - apiGroups: ["alicloud.com"] resources: ["*"] verbs: ["create", "delete", "get", "list", "patch", "update", "watch"] - apiGroups: ["policy"] resources: ["poddisruptionbudgets"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: ["networking.istio.io"] resources: ["*"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: ["config.istio.io"] resources: ["*"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: ["rbac.istio.io"] resources: ["*"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: ["istio.alibabacloud.com"] resources: ["*"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: ["authentication.istio.io"] resources: ["*"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: ["log.alibabacloud.com"] resources: ["*"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: ["monitoring.kiali.io"] resources: ["*"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: ["kiali.io"] resources: ["*"] verbs: ["create", "delete", "deletecollection", "get", "list", "patch", "update", "watch"] - apiGroups: ["apiextensions.k8s.io"] resources: ["customresourcedefinitions"] verbs: ["get", "list", "create", "watch", "patch", "update", "delete", "deletecollection"] - apiGroups: ["serving.knative.dev"] resources: ["*"] verbs: ["get", "list", "create", "watch", "patch", "update", "delete", "deletecollection"] - apiGroups: ["eventing.knative.dev"] resources: ["*"] verbs: ["get", "list", "create", "watch", "patch", "update", "delete", "deletecollection"] - apiGroups: ["messaging.knative.dev"] resources: ["*"] verbs: ["get", "list", "create", "watch", "patch", "update", "delete", "deletecollection"] - apiGroups: ["sources.eventing.knative.dev"] resources: ["*"] verbs: ["get", "list", "create", "watch", "patch", "update", "delete", "deletecollection"] - apiGroups: ["tekton.dev"] resources: ["*"] verbs: ["get", "list", "create", "watch", "patch", "update", "delete", "deletecollection"] - apiGroups: ["alert.alibabacloud.com"] resources: ["*"] verbs: ["get", "list", "create", "watch", "patch", "update", "delete", "deletecollection"]
場(chǎng)景三:授權(quán)對(duì)象為集群內(nèi)應(yīng)用的權(quán)限管理員
授權(quán)對(duì)象需要管理其他RAM用戶或RAM角色的RBAC權(quán)限。默認(rèn)情況下,RAM用戶或RAM角色不具備對(duì)其他RAM用戶或RAM角色授權(quán)RBAC的權(quán)限。當(dāng)授權(quán)對(duì)象進(jìn)入容器計(jì)算服務(wù)控制臺(tái)授權(quán)管理頁面時(shí),如果界面提示當(dāng)前子賬號(hào)不具備授權(quán)管理權(quán)限,請(qǐng)聯(lián)系主賬號(hào)或權(quán)限管理員授權(quán),則說明授權(quán)對(duì)象缺少必要的RAM授權(quán)或?qū)旱腞BAC管理員授權(quán)。
RAM授權(quán)
需要確保授權(quán)對(duì)象被授予必要的RAM權(quán)限,策略內(nèi)容需要包括:
列舉其他RAM用戶或RAM角色
給指定RAM用戶或RAM角色授予RAM權(quán)限策略
查看指定RAM用戶或RAM角色的Kubernetes RBAC權(quán)限配置
Kubernetes RBAC授權(quán)能力
您需要登錄RAM管理控制臺(tái),為指定RAM用戶或RAM角色授予相應(yīng)的RAM權(quán)限,具體操作,請(qǐng)參見為RAM用戶或RAM角色授予RAM權(quán)限。RAM自定義策略內(nèi)容示例如下所示。
{ "Statement": [ { "Effect": "Allow", "Action": [ "acc:DescribeCommodityStatus", "acc:CheckServiceRole", "acc:DescribeCloudProducts", "acc:DescribeRegions", "acc:DescribeZones", "acc:GetInstancePrice" ], "Resource": "*" }, { "Effect": "Allow", "Action": "bssapi:GetPayAsYouGoPrice", "Resource": "*" }, { "Action": [ "ram:Get*", "ram:List*", "cs:GetUserPermissions", "cs:GetSubUsers", "cs:GrantPermission" ], "Resource": "*", "Effect": "Allow" }, { "Action": [ "ram:AttachPolicyToUser", "ram:AttachPolicyToRole" ], "Effect": "Allow", "Resource": [ "acs:ram:*:*:policy/xxxx", # xxxx需要替換成您需要綁定的RAM策略名稱。如果您替換成*,表示授權(quán)對(duì)象擁有所有RAM策略的授權(quán)綁定能力。 "acs:*:*:*:user/*" ] }, { "Action": [ "vpc:ListEnhanhcedNatGatewayAvailableZones", "vpc:DescribeEipAddresses" ], "Effect": "Allow", "Resource": "*" } ], "Version": "1" }RBAC授權(quán)
需要為授權(quán)對(duì)象配置目標(biāo)集群和對(duì)應(yīng)命名空間的訪問權(quán)限為管理員或者自定義角色中的cluster-admin。
說明阿里云賬號(hào)(即主賬號(hào))和集群創(chuàng)建者會(huì)默認(rèn)綁定cluster-admin,擁有集群內(nèi)所有Kubernetes資源對(duì)象的訪問權(quán)限。
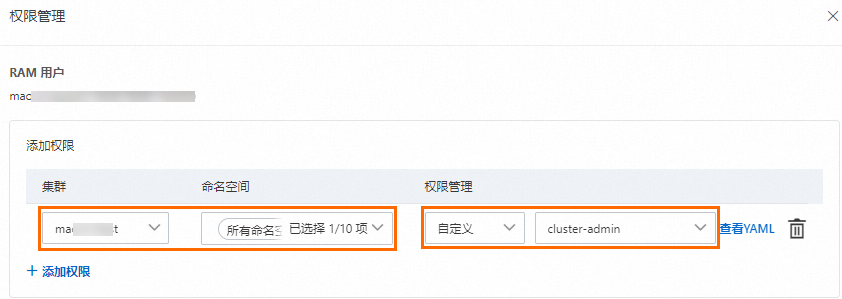
當(dāng)您對(duì)授權(quán)對(duì)象完成了上述RAM授權(quán)和RBAC授權(quán)后,即可擁有對(duì)其他RAM用戶或RAM角色在指定權(quán)限范圍內(nèi)的RBAC授權(quán)管理能力。具體操作,請(qǐng)參見為RAM用戶或RAM角色授予RAM權(quán)限。
鑒權(quán)Action說明
權(quán)限名稱(Action) | 說明 |
acc:CheckServiceRole | 檢查賬號(hào)是否授權(quán)產(chǎn)品通過角色扮演,訪問其他云資源賬號(hào)的ServiceRole。 |
acc:DescribeCommodityStatus | 檢查賬號(hào)是否已開通ACS產(chǎn)品。 |
權(quán)限名稱(Action) | 說明 |
bssapi:GetPayAsYouGoPrice | 查詢后付費(fèi)產(chǎn)品詢價(jià)服務(wù)。 |
ram:ListUserBasicInfos | 查詢所有RAM用戶的基本信息。 |
ram:ListRoles | 查詢所有RAM角色的基本信息。 |
容器服務(wù)ACK鑒權(quán)Action說明,請(qǐng)參考授權(quán)信息。
該文檔僅供授權(quán)參考,具體授權(quán)規(guī)則請(qǐng)您詳細(xì)了解容器服務(wù)ACK鑒權(quán)Action說明授權(quán)信息后,滿足最小授權(quán)原則為前提,根據(jù)實(shí)際需要編寫。
如果授權(quán)不指定目標(biāo)集群ID,選擇授權(quán)范圍“*”,將代表授權(quán)除ACS類型以外所有ACK集群的操作權(quán)限,請(qǐng)謹(jǐn)慎授權(quán)。